Figure 1. IP routing is done hop-by-hop.


In our previous discussion, Introducing the Router, I explained what a router is and a little bit about how it works. In this article, I'm going to pick up that thread and discuss routing protocols.
Routing protocols implement algorithms that tell routers the best paths through internetworks. Routing protocols include Border Gateway Protocol (BGP), Interior Gateway Routing Protocol (IGRP), Routing Information Protocol, and Open Shortest Path First (OSPF) to name a few. Routing protocols provide the layer 3 network state update. Protocols that are transported through a network, such as Internet Protocol (IP), Novell Internetwork Packet eXchange (IPX), and AppleTalk are called routed protocols.
In short, routing protocols route datagrams through a network. Routing is a layer 3 function, thus, routing and routed protocols are network-layer entities. Routing tables on the layer 3 switch (router) are populated by information from routing protocols. A routed protocol will enter an interface on a router, be placed in a memory buffer, then it will be forwarded out to an interface based on information in the routing table.
The IP protocol is the most common of the routed protocols. AppleTalk and Novell IPX still exist in some networks but are no longer as common as they were a few years ago. How does a routed protocol behave? Let’s examine an IP packet in our fictitious Sprockets corporate network.
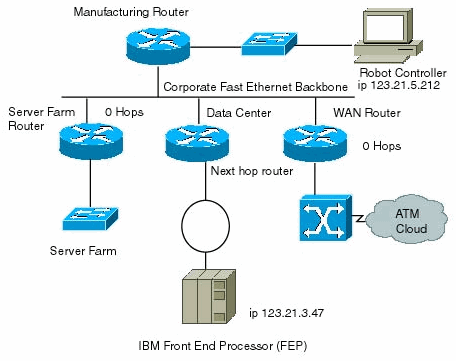
In this example, an Intel PC controlling robot, on the manufacturing floor segment of the Sprockets’ network, will make a database query to an IBM mainframe host, on the data center network segment. The manufacturing segment media is fast Ethernet and the IBM host segment is on token ring. A layer 3 IP datagram will have traverse different layer 2 encapsulations and layer 1 media.
|
|
Also in Networking as a 2nd Language: Layer 3 Switching -- Introducing the Router Understanding Spanning Tree Protocol -- the Fundamental Bridging Algorithm |
Both the IBM mainframe and the manufacturing floor robot controller
are configured to use the layer 3 IP routed protocol. The IP datagram,
originating in the controller PC, assigns the destination address of 123.21.3.47,
the IP address of the IBM mainframe. The IP datagram is encapsulated in
a layer 2 Ethernet frame and placed onto the wire. The beauty of the IP
protocol is that a datagram doesn’t know how to directly get to its
destination. This is the work of a routing protocol.
The Sprocket’s manufacturing router has network segment 123.21.5.0
directly connected to one of its fast Ethernet interfaces, FE1. The
router sees the IP datagram as it enters on interface FE1. The router
tears off the layer 2 Ethernet frame and reads the destination address,
123.21.3.47.
The Sprocket’s network is using Enhanced Interior Gateway Routing
Protocol, EIGRP, for its network path algorithm. The router examines
its routing table and determines that the IP datagram’s next hop should
be to the neighboring data center router, which advertises a route to
segment 123.21.3.0.
Based on the routing table, the datagram needs to be forwarded out
through fast Ethernet interface FE0. Interface FE0 advertises a path to
the desired 123.21.5.0 subnet, see Figure 2. The datagram
is then encapsulated in a fast Ethernet frame and sent out interface
FE0. Hop-by-hop, the IP datagram is handed off by routers in this
manner until the datagram reaches its destination network segment. The
idea of hops is to get the packet one hop closer each time through the
network.
|
The next hop for the example IP datagram is the data center router,
on the fast Ethernet backbone, interface FE0. The datagram’s
destination address is again examined. The Data Center router examines
its routing table and learns that segment 123.21.3.0 is
directly connected on its token ring interface, TR1. The datagram is
then encapsulated for token ring and is sent out the token ring
interface. The IBM mainframe listens on the wire and picks up the token
ring frame from the router. The frame is removed and the IP datagram is
processed.
You will notice that the IP addressing, is a layer 3 consistency in the Sprocket’s network. But, the layer 2 topology was mixed with fast Ethernet and token ring architecture. The routers handled the crossing of media. The IP datagram wasn’t involved with this process.
|
To learn how this was done, we’ll need to schedule a meeting with Nanna Spacely, who is now extremely busy at Sprockets as the lead network design engineer. After a discussion with Nanna, we learn she made the following configurations on the manufacturing router and data center router.
|
Nanna has provided us with the following configuration from the
manufacturing floor router. Although Nanna is a stickler for
fault-tolerant networks, which means there is a second router on the
manufacturing floor with similar connections, she only provides the
configuration for one of these routers. The routers are Cisco routers
running Cisco IOS software. Nanna uses the Cisco IOS exec mode command sh run to display the running configuration in her manufacturing floor router.
manfloor1# sh run
ip routing
!
interface FastEthernet 0
ip address 123.21.1.11 255.255.255.0
!
interface FastEthernet 1
ip address 123.21.5.11 255.255.255.0
!
router eigrp 41
network 123.0.0.0Likewise, the data center is fault tolerant and uses two backbone routers. We’ll examine only one configuration here.
datacenter1# sh run
ip routing
!
!
interface FastEthernet 0
ip address 123.21.1.21 255.255.255.0
!
interface TokenRing 1
ip address 123.21.3.21 255.255.255.0
!
router eigrp 41
network 123.0.0.0The key points of the configuration of these two routers are that the interfaces are all configured using an IP address scheme. The routing protocol is EIGRP with an autonomous system number of 41. The autonomous system number is a networking scheme that designates a logical networking domain. Routers inside this domain can only communicate with other routers in the same domain or autonomous system. However, routers can be configured to communicate with other routers outside their domain. An example of this would be the Sprockets’ firewall router Nanna plans to implement to allow access to the World Wide Web.
|
For the moment, all the routers in the Sprockets’ corporate network only communicate with devices in the autonomous system 41. This is a number Nanna used arbitrarily in her network design to identify her autonomous system. Networked devices inside the Sprockets’ corporate network domain can now communicate with each other using IP addressing schemes. Some of these concepts I have left a bit nebulous, such as IP and IP addressing. This will be the subject of our next installment of Networking as a Second Language.
Michael J. Norton is a software engineer at Cisco Systems.
Read more Networking as a 2nd Language columns.
Return to the O'Reilly Network.
Copyright © 2004 O'Reilly Media, Inc.