I’ve really been enjoying the feedback on the free wireless access from my neighbors. As always, everytime I start a new hobby, I end up with a handful of new toys – and I got one just today:

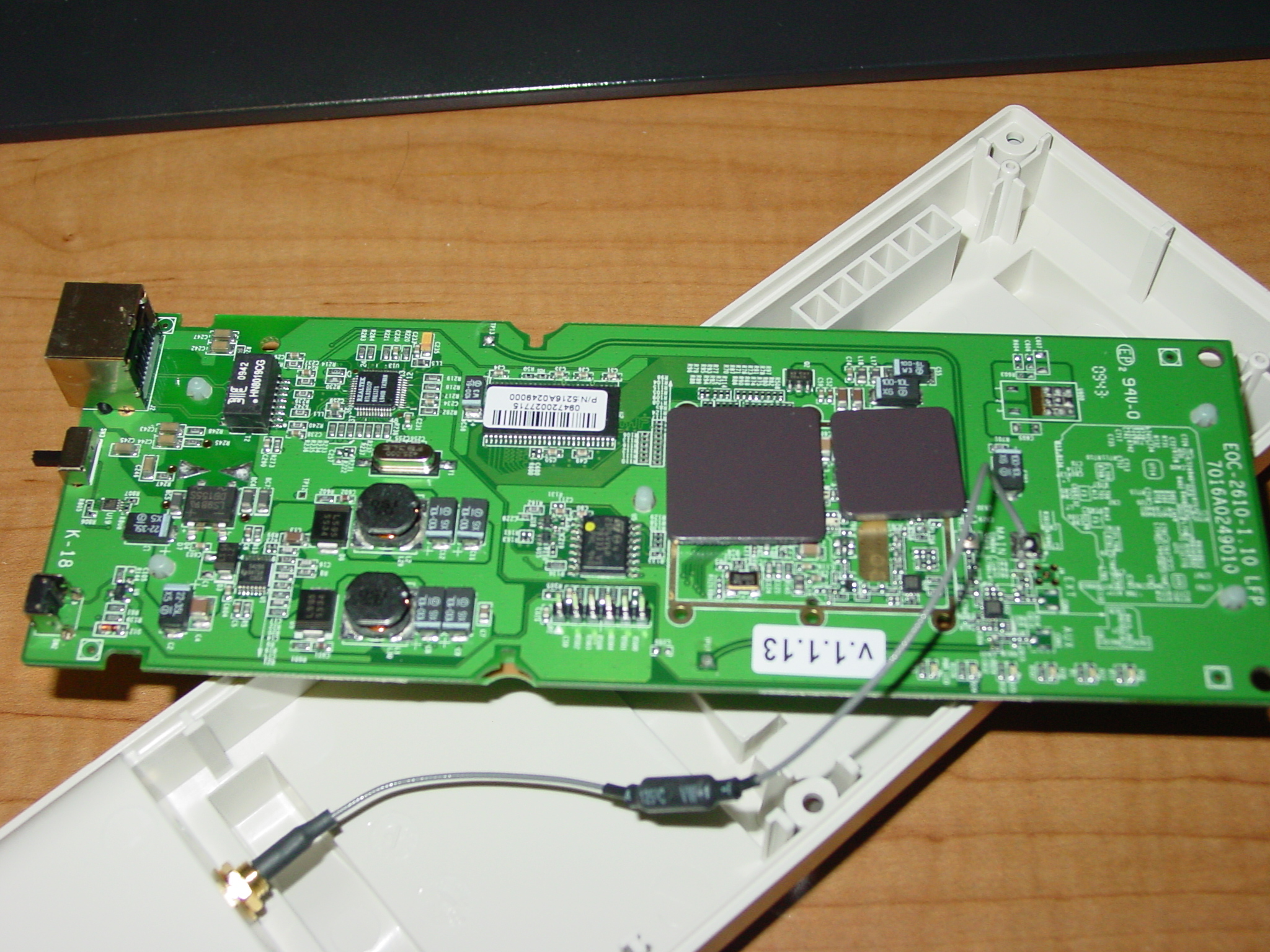
The Wi-Spy 2.4x is a portable USB spectrum analyzer for the 2.4Ghz range (They have other models that cover 900mhz and 2.4/5Ghz). The 2.4x model includes an external antenna (SMA), whereas the 2.4i has an internal antenna only.
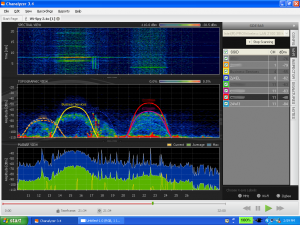
With the use of a wireless card, one can overlay SSID’s atop the channels in the Topographical graph and determine what radiation belongs to which Access Point. The bottom graph (Planar view) allows one to view which Zigbee channel, wifi channel, or frequency range is most in use.
There’s a similar device on the market which is substantially cheaper, the Airview, manufactured by Ubiquiti Networks (~$39 vs. ~$160), but from what I’ve seen, the Chanalyzer sofware in use with the Wi-Spy appears to have more features (the ability to record your captures, the ability to overlay RF “fingerprints” of various devices atop your captures), etc. The Airview software is written in Java (Read: supported in Linux), whereas Chanalyzer is written in .NET (good luck with that one under WINE).
There are Linux tools for use with the Wi-Spy (Spectrum-Tools) which I can defnitely appreciate, but again the recording/playback and fingerprinting along with SSID overlays really make Chanalyzer nice. (For the record, you can actually record the data using one of the tools in the Spectrum Tools suite… I don’t believe you can playback easily though)
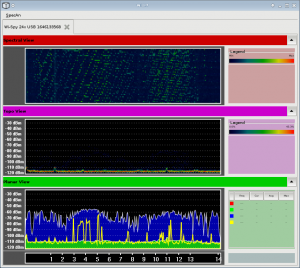
I’m supposed to be working on a number of other things at the moment (studying for an exam being the major item on my to-do list) so unfortunately this post is more of a “guess what I just got” as opposed to a “look at what this can do”. In the next few weeks, I plan on picking up an AirView also, and will provide a side-by-side comparison of the two.
In the meantime, check out this video advertising the Wi-Spy, and if you have any experience, recommendations or thoughts on it or the AirView – hit me up in the comments.