I’ve been fascinated with insects since I was in elementary school and had the opportunity to visit a bee farm. The descriptions of how bees worked together along with seeing a hive behind glass has stuck with me for years – the queen bee’s abdomen colored by nail polish to make her easily identifiable.

The Uncle Milton ant farm was the safest thing I could get as an alternative to my own bee colony, but it wasn’t until I was in my twenties that I finally received one as a gift. It wasn’t the classic green ant farm, but rather a gel ant farm. This further sparked my fascination with ants, but the harvester ants without a queen didn’t live very long.

In my quest to learn more and more about ants, I’ve stumbled across some amazing online resources: The Ants Canada Youtube Channel, AntWiki, Antfarm Yuku, etc. It wasn’t long before I joined the “build your own ant formicarium” craze.

Over the years I attempted to build a number of plaster cast nests, but I was never able to get the build just right. Then I found Tar Heel Ants formicariums. These formicaria are built with keeping humidity levels in line with the needs of ant colonies – something I seriously struggled with in each of my homemade solutions.

Ants are only fun if you can watch them – and that’s when a number of my projects merged together.
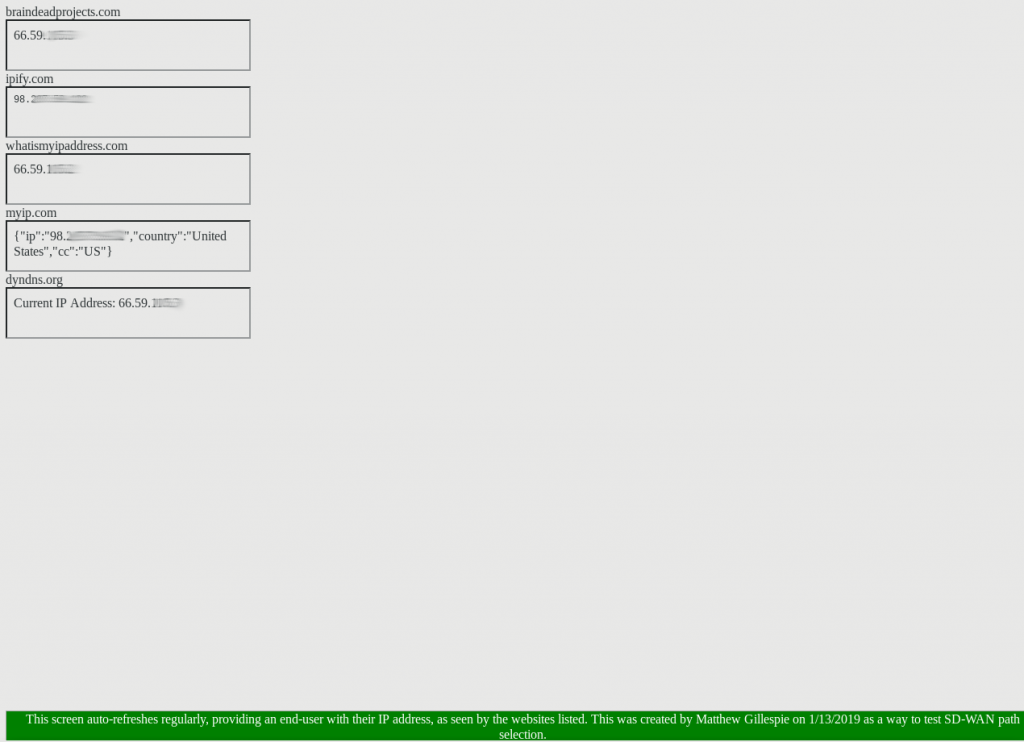
Inside my formicariums, the humidity was always too low. The humidity in my basement, on the other hand, always seemed high. When I decided to purchase a dehumidifier I wanted to measure it’s actual impact over time on my damp basement. I started a project I called “ThermoBots” to use a Raspberry Pi 2B with 2302 Temperature/Humidity sensor and create my own home environmental monitoring project.

The recipe is simple: A python/Django web application running under Apache that returns temperature and humidity values in JSON format. My home PRTG server polls and graphs these values over time.
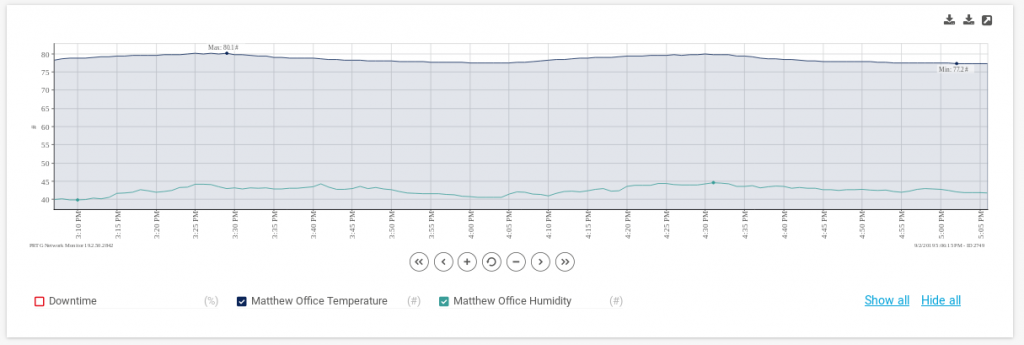
Once I created one “thermobot” I simply cloned it and now have monitoring for my loft, basement, server rack, and home office – where the “AntStudio” sits.

The Ant Studio is a large reptile terrarium that I’ve repurposed to house multiple Tar Heels’ Mini Hearth terrariums. The overhead vitamin D light is connected to a TP-Link SmartPlug mini, with a schedule set to activate the “Ant Sun” between 7am and 9pm.
Between 9pm and 7am, the “Ant Sun” it turned off and the “Ant Moon” is activated. The “Ant Moon” is simply a pair of IR floodlights.
I’ve attached four miniature IP Cameras (ELP-POE-1882’s with 1080p resolution) to a small piece of 2×3 lumber. These cameras have a great feature – while they don’t have an IR emitter, they support IR and thus I can view the nocturnal habits of my ants.

The cameras are powered via their ethernet cables, which connect to a Cisco 3750G POE switch. I have varifocal lenses attached to each camera that allow me to zoom in and out to perfect focus as I move the cameras around by hand.
I’ve included a few other items in the build, including a reptile heat mat that can also be controlled by TP-Link SmartPlugs, and because my 3rd floor office has a window air-conditioner to offset my home AC – I’ve covered the walls with reptile mat for insulation.
I’ve written two small bash script templates that leverage ffmpeg and allow me to record either the full video of an antcamera, or a timelapsed version to disk. The timelapse version runs daily creating an overview video of the day for me to watch at a later time.
At the 1:25 mark you can see the Ant Moon being turned on.
Script to record a timelapse video:
!/bin/bash
#Creates a timelapse video of an “AntCam”
#Create DNS entries for each camera, and symlink to this script in the form of “record–timelapse.sh”
#Usage: record–timelapse.sh
DATESTAMP=$(date +%Y-%m-%d-%H-%M)
DIR=”/virtualmachines/Ants/”
CAMERA=$(echo $0 | egrep -o “antcam[0-9]+”)
HOSTNAME=”$CAMERA.braindeadhomebase.net”
PASSWORD=”SUPERSECRETPASSWORD”
DURATION=”$1″
cd $DIR
timeout $DURATION /usr/bin/ffmpeg -nostdin -i rtsp://$HOSTNAME:554//user=admin_password=$PASSWORD_channel=1_stream=0.sdp -vf “select=gt(scene\,0.004),setpts=N/(25*TB)” $DIR/$CAMERA-timelapse-$DATESTAMP.mp4
exit
Script to record a full video:
!/bin/bash
# Creates a full video of an “AntCam”
#Create DNS entries for each camera, and symlink to this script in the form of “record-.sh”
#Usage: record-.sh
DATESTAMP=$(date +%Y-%m-%d-%H-%M)
DIR=”/virtualmachines/Ants/”
CAMERA=$(echo $0 | egrep -o “antcam[0-9]+”)
HOSTNAME=”$CAMERA.braindeadhomebase.net”
PASSWORD=”SUPERSECRETPASSWORD”
DURATION=”$1″
cd $DIR
/usr/bin/timeout $DURATION /usr/bin/nice –5 /usr/bin/ffmpeg -nostdin -i rtsp://$HOSTNAME:554//user=admin_password=$PASSWORD_channel=1_stream=0.sdp $DIR/$CAMERA-full-$DATESTAMP.mp4
exit
I’ve raised a handful of colonies with mixed success over the years: Tapinoma Sessile, Prenolepis Imperis, Crematagaster Cerasi. At the moment, I have two successful colonies – Pogonomyrmex Occidentalis (50+ workers) and Camponotus Pennsylvanicus (20+ workers). I’ve learned a lot about how best to care for them, if you’re new to the hobby here are some of my recommendations:
- The Mini Hearths from Tar Heels ants solve the problem I repeatedly encountered with creating a suitable living environment. Check the water in the tower regularly.
- Ants need carbohydrates. Initially I was feeding them honey in a straw, but the liquid feeders from byFormica work great. I use the micro sized feeders along with the byFormica Sunburst Ant Nectar.
- Be careful what food you use – I’ve accidentally introduced some things that were harmful. Freeze dried meal worms and crickets, as well as Flukers gourmet style meal worms and crickets seem to work well.
- My colonies LOVE live wingless fruit flies. It’s also fun to watch them hunt.
- For the Pogo’s dandelion seeds are very popular. Be careful when introducing seeds to test them first and ensure there are no harmful pesticides present. Do this by separating a few ants with the food source for a few days as a test.
- Fluon works great as barrier to keep your ants from escaping. I had mixed success with baby powder and rubbing alchohol, but Fluon keeps both the ants and fruit flies from climbing too high and risking escape. My experience is that it wears down after about a year, but it’s easily re-applied.
- Get a USB vacuum cleaner and connect a large piece of tubing to it. It makes cleaning the formicarium’s much easier.
- Having an aspirator to collect any ants that escape when moving tubing around is extremely helpful. Make sure you have it ready.
I’m working on uploading daily videos to this site. In the meantime, here’s one final video of feeding time: